Insider Threat Protection Market – Growth of Market Size, Market Dynamics, Trends, Segments and Forecast Period (2025-2032)
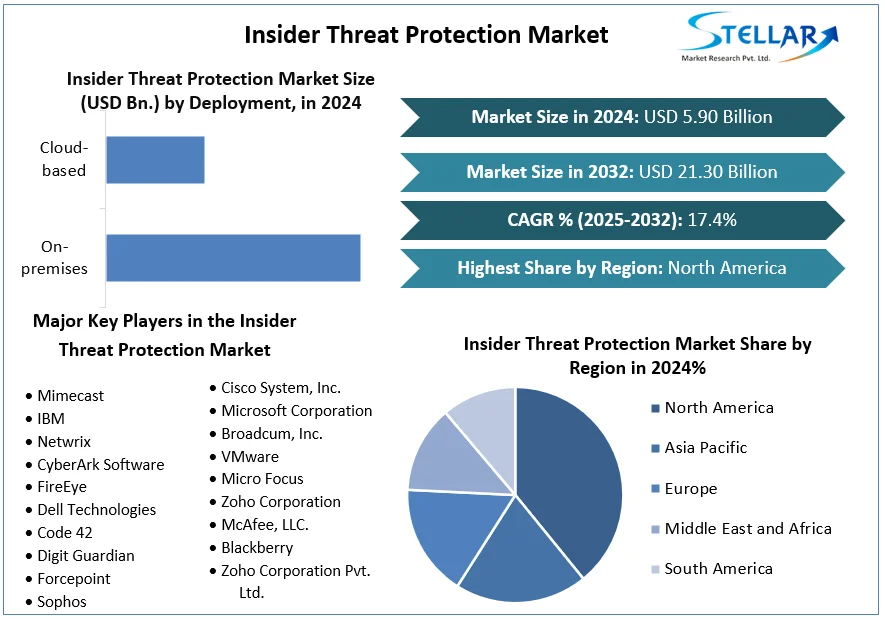
The Insider Threat Protection Market Size is valued at 5.90 billion in 2024 and is expected to reach 21.30 billion by the year 2032 at a 17.4 % CAGR during the forecast period for 2025-2032.
Format : PDF | Report ID : SMR_1485
Insider Threat Protection Market Overview
Solutions, deployments, enterprise sizes, verticals, and geographic regions are used to segment the Insider Threat Protection market. User activity monitoring, data loss prevention, and security information and event management (SIEM) are other sub-segments of the solution segment. On-premises and cloud-based deployment are further sub-segmented within the deployment segment. Small and medium-sized enterprises (SMEs) and large enterprises are further divided into the enterprise size segment. The vertical section is further divided into the BFSI, healthcare, government, IT and telecom, and other sectors. Due to the presence of numerous government organisations and IT firms, the North American region is anticipated to continue to dominate the market over the projection period.
Due to the region's expanding adoption of digital technologies and increased awareness of the insider threat scenario, the Asia Pacific region is anticipated to experience the quickest growth during the projection period. For organisations of all sizes to safeguard their data and systems from insider threats, Insider Threat Protection solutions are crucial. Malicious workers, contractors, or other authorised users may be the source of insider threats. Before insider threats can do any harm, organisations can identify, detect, and respond to them with the aid of Insider Threat Protection technologies.
To get more Insights: Request Free Sample Report
Insider Threat Protection Market Dynamics: Drivers, Opportunities, Challenges and Restraints
Incidents involving insider threats are rising, with malicious insiders being responsible for a sizable part of data breaches. This is brought on by a variety of elements, such as the sophistication of insider assaults, the rise in remote workers, and the importance of data. Organisations are investing in Insider Threat Protection solutions to reduce risk as they become more aware of the dangers of insider threats. Numerous variables, like as high-profile insider threat cases, legal compliance requirements, and the rising cost of data breaches, are driving this. As Insider Threat systems get more complex, organisations find it harder to identify and stop insider threats. Organisations can monitor user activity with the aid of Insider Threat Protection technologies to spot suspicious activities. The Insider Threat Protection industry is also being driven by the growing use of cloud computing. Platforms for cloud computing provide many advantages, such as scalability, agility, and cost savings.
However, they also bring about fresh security issues, such as the possibility of insider threats. Insider Threat Protection solutions can assist businesses in safeguarding their cloud-based data. Governments all over the world are passing laws requiring businesses to safeguard their data from insider threats. This is encouraging businesses across all sectors to use Insider Threat Protection solutions. New technologies' emergence Insider Threat Protection solutions are becoming increasingly complex because to the adoption of new technologies like artificial intelligence and machine learning.
These solutions can aid businesses in identifying and averting insider risks. Because data is becoming more valuable, businesses are spending more to safeguard it from dangers of various kinds, including insider threats. Business operations are being conducted in increasingly globalised environments, which increases their susceptibility to insider attacks. Regardless of where they are located, Insider Threat Protection solutions can assist organisations in protecting their data from insider threats.
Insider Threat Protection Market Opportunities
Insider attacks' rising frequency and sophistication. Data breaches are now mostly caused by insider assaults, which are growing more sophisticated and challenging to identify. The expanding use of cloud computing and other technologies for distant work. Because employees can now access private information from anywhere in the world, these technologies have increased the attack surface for insider threats. The increased need for regulatory compliance. Regulations that mandate the implementation of Insider Threat Protection solutions in order to safeguard sensitive data are currently applicable to several sectors. Solutions for Insider Threat Protection in the cloud. Since they provide several benefits over on-premises solutions, such as scalability, flexibility, and ease of deployment, cloud-based Insider Threat Protection solutions are growing in popularity.
Insider Threat Protection solutions that make use of machine learning and artificial intelligence (AI). Insider Threat Protection systems that are better at detecting and preventing insider assaults can be created using AI and ML. AI and ML, for instance, can be used to analyse user behaviour and spot unusual activity that can be a sign of an insider attack. Insider Threat Protection solutions that are combined with additional security measures. Numerous benefits, including enhanced visibility and control over security concerns, are provided by integrated Insider Threat Protection systems. To ensure that only authorised users have access to sensitive data, for instance, Insider Threat Protection solutions can be integrated with identity and access management (IAM) solutions.
Insider Threat Protection Market Challenges
They might originate from a wide range of people, including malevolent employees, independent contractors, and outside vendors, insider attacks can be challenging to identify and prevent. It may also be possible for insiders to have authorised access to sensitive data and systems, making it more challenging to recognise and thwart their attacks. Insider Threat Protection solutions are still rather new and developing; there isn't a universally applicable solution. Insider Threat Protection solutions that match an organization's unique objectives and criteria must be properly chosen and implemented. Implementing and maintaining Insider Threat Protection solutions can be expensive, particularly for small and medium-sized enterprises. For some organisations, this may act as an impediment to adoption. Many organisations are not well-versed in the insider danger or its mitigation. This may result in insufficient Insider Threat Protection safeguards and raised danger of insider attacks. Insider Threat Protection solutions are capable of gathering and analysing a lot of information about employee behaviour.
Organisations must make sure they are employing Insider Threat Protection solutions in a legal and moral manner because this could lead to privacy concerns. There is a talent scarcity for Insider Threat Protection professionals, which can make it challenging for organisations to recruit and keep the skills they require to successfully adopt and operate Insider Threat Protection systems. Organisations must abide by a number of laws and rules while collecting, using, and storing employee data. Insider Threat Protection solution implementation and use may become more difficult as a result. For Insider Threat Protection solutions to be effective, they must be integrated with other security systems like firewalls and intrusion detection systems. This can be difficult, especially for businesses with intricate IT infrastructures.
Insider Threat Protection Market Restraints
Implementing and maintaining Insider Threat Protection solutions can be difficult and expensive. For smaller organisations with fewer resources, this could be a hurdle. Some businesses might not be aware of the internal threat or how crucial Insider Threat Protection solutions are. Because of their ignorance, businesses may undervalue and neglect to invest in Insider Threat Protection. Insider Threat Protection solutions are capable of gathering and tracking a variety of user data. Employees and organisations may become concerned about privacy as a result. Insider Threat Protection specialists that possess the necessary skills are in short supply. This can make it challenging for businesses to attract and keep the personnel they require to successfully adopt and manage Insider Threat Protection solutions. By selecting Insider Threat Protection solutions that are catered to their unique demands and budget, organisations can get around the complexity and cost of Insider Threat Protection solutions. They can also collaborate with seasoned Insider Threat Protection service providers to properly implement and manage their solutions.
By teaching their employees and stakeholders about the risks and advantages of Insider Threat Protection, organisations may increase awareness of the insider threat and the significance of Insider Threat Protection solutions. Additionally, they can take part in trade shows and forums to converse with other businesses about their Insider Threat Protection experiences. Businesses can solve privacy issues by putting in place Insider Threat Protection systems that are open and offer staff member’s access over their data. Additionally, they need to create explicit policies and guidelines for using Insider Threat Protection solutions. Businesses can fill the skills gap by funding IT employee training and development initiatives. To acquire the assistance they require for the implementation and management of their Insider Threat Protection solutions, companies can also collaborate with knowledgeable Insider Threat Protection providers.
Insider Threat Protection Market Trends
The sophistication and frequency of insider attacks, which are rising. Because dangerous insiders are using more advanced techniques, insider threats are getting harder to identify and avoid. As a result, businesses are spending more on Insider Threat Protection solutions to safeguard themselves against insider threats. The expanding use of mobile devices and cloud computing. Organisations now have a larger attack surface thanks to the move to cloud computing and mobile devices since data may now be accessed from outside the confines of the conventional network perimeter. Because of this, it is more challenging for businesses to keep tabs on user behaviour and stop employees from stealing information. The increased need for regulatory compliance. Regulations that apply to many businesses mandate the use of Insider Threat Protection systems to safeguard sensitive data. Insider Threat Protection solutions are in high demand across a variety of sectors, including government, healthcare, and financial services. The expanding usage of machine learning (ML) and artificial intelligence (AI).
Insider Threat Protection solutions that are more advanced and capable of better detecting and preventing insider assaults are being developed using AI and ML. AI and ML, for instance, can be used to analyse user behaviour and spot unusual activity that can be a sign of an insider attack. Insider Threat Protection’s integration with other security measures. Insider Threat Protection systems are rapidly being connected with other security tools, such as user behaviour analytics (UBA) and security information and event management (SIEM) tools. This enables organisations to have a more comprehensive understanding of their security posture and to more effectively recognise and counter insider threats. The increased significance of knowledge and education about insider threats. Insider threat awareness and training are becoming more and more important to organisations. By educating employees about the dangers and how to avoid them, this is assisting in lowering the chance of insider attacks.
Insider Threat Protection Market Regional Analysis
North America: Due to the huge concentration of technological firms, financial institutions, and governmental organisations in North America, the region dominates the market for insider threat protection. The adoption of insider threat protection solutions has been accelerated by the region's strong regulatory framework and cyber security ecosystem.
Europe: Increased awareness of insider threats and strict data protection laws like GDPR are driving the steady growth of the insider threat protection market in Europe. To protect sensitive information, sectors like finance, healthcare, and manufacturing are investing in these solutions.
Asia-Pacific: The market for insider threat protection is expanding quickly in the Asia-Pacific region, driven by corporate growth, initiatives for digital transformation, and an increase in cyber-attacks. Japan, China, and India are among the major contributors to this expansion.
South America: Latin America is gradually realising the need of protecting against insider threats, especially in industries like banking where data security is crucial. Businesses in this region are investing more in preventive measures as cyber threats change.
Middle East and Africa: Due to the necessity to protect vital infrastructure and comply with data protection rules, the Middle East and Africa area is also catching up in the use of insider threat protection. One significant player in this area is the oil and gas industry.
Insider Threat Protection Market Segment Analysis
By Solution: UEBA systems track user behaviour and look for unusual patterns that can point to an insider threat. DLP solutions stop the purposeful or unintentional exfiltration of sensitive data from the organisation. Endpoint detection and response (EDR) technologies identify harmful behaviour on endpoints like servers and laptops and take appropriate action. SIEM stands for security information and event management. SIEM solutions gather and analyse security data from all throughout the company to find threats and trends.
By Deployment: Insider Threat Protection solutions that are installed and managed on-site use the infrastructure that belongs to the company. The provider hosts and manages cloud-based Insider Threat Protection solutions.
By Enterprise Size: Small and medium-sized businesses (SMEs) may prefer cloud-based Insider Threat Protection solutions because they often have fewer resources to devote to security. Since they frequently have more resources to devote to security, large businesses may favour on-premises Insider Threat Protection solutions or a hybrid strategy.
By Vertical: Organisations in the financial sector handle a lot of sensitive data, making them particularly vulnerable to insider threats. Organisations in the healthcare industry handle a lot of sensitive data, making them particularly vulnerable to insider attacks. Since government organisations handle a lot of sensitive data, insider threats are a serious concern for them as well. Various verticals Retail, manufacturing, and technology are additional industries with a high risk of insider attacks.
Insider Threat Protection Market Competitive Landscape
There is fierce competition in the Insider Threat Protection (ITP) sector, where a number of well-known and up-and-coming providers provide a wide range of solutions. As insider threats multiply and organisations become more aware of them, the insider threat market is anticipated to increase significantly over the next few years. With numerous established and up-and-coming manufacturers offering a wide range of solutions, the Insider Threat Protection industry is extremely competitive. The market is anticipated to expand significantly over the next few years due to the rise in insider threats and increased awareness of these concerns among organisations.
Dell Technologies: Our narrative began with a conviction and a passion: that anybody, anywhere in the globe, should have simple access to the best technology. Michael Dell's University of Texas dorm room was the location at the time. Today, Dell Technologies plays a significant role in reshaping the global digital landscape. We are one of the top technological firms in the world, using our exceptional talents to change people's lives. Everything we do has an influence on everyone and everywhere, from hybrid cloud solutions to high-performance computing to ambitious social impact and environmental efforts. The company had a revenue of 101.2 billion in 2022.
Code 42: Although we are not new to the cyber security world, our strategy for protecting against insider risk is. We have been preserving the concepts of the most creative businesses, including 18 of the most valuable brands in the world, for almost 20 years. And our data security solutions have changed as their needs—and the needs of their workforce—have done. Our team's current goal is to create solutions that were designed with the collaborative culture of today in mind. Our SaaS-based Insider Risk Management solutions reveal and prioritize file exposure and exfiltration events that reflect genuine business dangers, require investigation, and require a reaction by tracking activity across desktops, email, and the cloud. The Company had a revenue of 44.5 million in 2022.
|
Insider Threat Protection Market Scope |
|
|
Market Size in 2024 |
USD 5.90 Bn. |
|
Market Size in 2032 |
USD 21.30 Bn. |
|
CAGR (2025-2032) |
17.4 % |
|
Historic Data |
2019-2024 |
|
Base Year |
2024 |
|
Forecast Period |
2025-2032 |
|
Segment Scope |
By Solution
|
|
By Deployment
|
|
|
By Vertical
|
|
|
By Enterprise Size
|
|
|
Regional Scope |
North America- United States, Canada, and Mexico Europe – UK, France, Germany, Italy, Spain, Sweden, Austria, and Rest of Europe Asia Pacific – China, India, Japan, South Korea, Australia, ASEAN, Rest of APAC Middle East and Africa - South Africa, GCC, Egypt, Nigeria, Rest of the Middle East and Africa South America – Brazil, Argentina, Rest of South America |
Insider Threat Protection Market Key Players
- Mimecast
- IBM
- Netwrix
- CyberArk Software
- FireEye
- Dell Technologies
- Code 42
- Digit Guardian
- Forcepoint
- Sophos
- Fortinet
- Cisco System, Inc.
- Microsoft Corporation
- Broadcum, Inc.
- VMware
- Micro Focus
- Zoho Corporation
- McAfee, LLC.
- Blackberry
- Zoho Corporation Pvt. Ltd.
- Citrix Systems
Frequently Asked Questions
The Insider Threat Protection Market CAGR in 2024 was US$ 5.90 billion.
The Insider Threat Protection Market CAGR in 2032 is expected to US$ 21.30 billion.
The segments of Solution are User and entity behavior analytics, Data loss prevention, Endpoint detection and response and Security information & event management.
17.4 percentage is the CAGR for the forecast period (2025-2032) of Insider Threat Protection Market.
1. Insider Threat Protection Market: Research Methodology
2. Insider Threat Protection Market: Executive Summary
3. Insider Threat Protection Market: Competitive Landscape
3.1. SMR Competition Matrix
3.2. Competitive Landscape
3.3. Key Players Benchmarking
3.4. Market Structure
3.4.1. Market Leaders
3.4.2. Market Followers
3.4.3. Emerging Players
3.5. Consolidation of the Market
4. Insider Threat Protection Market: Dynamics
4.1. Market Trends by Region
4.1.1. North America
4.1.2. Europe
4.1.3. Asia Pacific
4.1.4. Middle East and Africa
4.1.5. South America
4.2. Market Drivers by Region
4.2.1. North America
4.2.2. Europe
4.2.3. Asia Pacific
4.2.4. Middle East and Africa
4.2.5. South America
4.3. Market Restraints
4.4. Market Opportunities
4.5. Market Challenges
4.6. PORTER’s Five Forces Analysis
4.7. PESTLE Analysis
4.8. Value Chain Analysis
4.9. Regulatory Landscape by Region
4.9.1. North America
4.9.2. Europe
4.9.3. Asia Pacific
4.9.4. Middle East and Africa
4.9.5. South America
5. Insider Threat Protection Market Size and Forecast by Segments (by Value USD and Volume Units)
5.1. Insider Threat Protection Market Size and Forecast, by Solution (2024-2032)
5.1.1. User and entity behaviour analytics
5.1.2. Data loss prevention
5.1.3. Endpoint detection and response
5.1.4. Security information and event management
5.2. Insider Threat Protection Market Size and Forecast, by Deployment (2024-2032)
5.2.1. On-premises
5.2.2. Cloud-based
5.3. Insider Threat Protection Market Size and Forecast, by Vertical (2024-2032)
5.3.1. Financial Services
5.3.2. Healthcare
5.3.3. Government
5.3.4. Other Verticals
5.4. Insider Threat Protection Market Size and Forecast, by Enterprise Size (2024-2032)
5.4.1. Small and medium sized enterprises
5.4.2. Large Enterprises
5.5. Insider Threat Protection Market Size and Forecast, by Region (2024-2032)
5.5.1. North America
5.5.2. Europe
5.5.3. Asia Pacific
5.5.4. Middle East and Africa
5.5.5. South America
6. North America Insider Threat Protection Market Size and Forecast (by Value USD and Volume Units)
6.1. North America Insider Threat Protection Market Size and Forecast, by Solution (2024-2032)
6.1.1. User and entity behaviour analytics
6.1.2. Data loss prevention
6.1.3. Endpoint detection and response
6.1.4. Security information and event management
6.2. North America Insider Threat Protection Market Size and Forecast, by Deployment (2024-2032)
6.2.1. On-premises
6.2.2. Cloud-based
6.3. North America Insider Threat Protection Market Size and Forecast, by Vertical (2024-2032)
6.3.1. Financial Services
6.3.2. Healthcare
6.3.3. Government
6.3.4. Other Verticals
6.4. North America Insider Threat Protection Market Size and Forecast, by Enterprise Size (2024-2032)
6.4.1. Small and medium sized enterprises
6.4.2. Large Enterprises
6.5. North America Insider Threat Protection Market Size and Forecast, by Country (2024-2032)
6.5.1. United States
6.5.2. Canada
6.5.3. Mexico
7. Europe Insider Threat Protection Market Size and Forecast (by Value USD and Volume Units)
7.1. Europe Insider Threat Protection Market Size and Forecast, by Solution (2024-2032)
7.1.1. User and entity behaviour analytics
7.1.2. Data loss prevention
7.1.3. Endpoint detection and response
7.1.4. Security information and event management
7.2. Europe Insider Threat Protection Market Size and Forecast, by Deployment (2024-2032)
7.2.1. On-premises
7.2.2. Cloud-based
7.3. Europe Insider Threat Protection Market Size and Forecast, by Vertical (2024-2032)
7.3.1. Financial Services
7.3.2. Healthcare
7.3.3. Government
7.3.4. Other Verticals
7.4. Europe Insider Threat Protection Market Size and Forecast, by Enterprise Size (2024-2032)
7.4.1. Small and medium sized enterprises
7.4.2. Large Enterprises
7.5. Europe Insider Threat Protection Market Size and Forecast, by Segment5 (2024-2032)
7.6. Europe Insider Threat Protection Market Size and Forecast, by Country (2024-2032)
7.6.1. UK
7.6.2. France
7.6.3. Germany
7.6.4. Italy
7.6.5. Spain
7.6.6. Sweden
7.6.7. Austria
7.6.8. Rest of Europe
8. Asia Pacific Insider Threat Protection Market Size and Forecast (by Value USD and Volume Units)
8.1. Asia Pacific Insider Threat Protection Market Size and Forecast, by Solution (2024-2032)
8.1.1. User and entity behaviour analytics
8.1.2. Data loss prevention
8.1.3. Endpoint detection and response
8.1.4. Security information and event management
8.2. Asia Pacific Insider Threat Protection Market Size and Forecast, by Deployment (2024-2032)
8.2.1. On-premises
8.2.2. Cloud-based
8.3. Asia Pacific Insider Threat Protection Market Size and Forecast, by Vertical (2024-2032)
8.3.1. Financial Services
8.3.2. Healthcare
8.3.3. Government
8.3.4. Other Verticals
8.4. Asia Pacific Insider Threat Protection Market Size and Forecast, by Enterprise Size (2024-2032)
8.4.1. Small and medium sized enterprises
8.4.2. Large Enterprises
8.5. Asia Pacific Insider Threat Protection Market Size and Forecast, by Country (2024-2032)
8.5.1. China
8.5.2. S Korea
8.5.3. Japan
8.5.4. India
8.5.5. Australia
8.5.6. Indonesia
8.5.7. Malaysia
8.5.8. Vietnam
8.5.9. Taiwan
8.5.10. Bangladesh
8.5.11. Pakistan
8.5.12. Rest of Asia Pacific
9. Middle East and Africa Insider Threat Protection Market Size and Forecast (by Value USD and Volume Units)
9.1. Middle East and Africa Insider Threat Protection Market Size and Forecast, by Solution (2024-2032)
9.1.1. User and entity behaviour analytics
9.1.2. Data loss prevention
9.1.3. Endpoint detection and response
9.1.4. Security information and event management
9.2. Middle East and Africa Insider Threat Protection Market Size and Forecast, by Deployment (2024-2032)
9.2.1. On-premises
9.2.2. Cloud-based
9.3. Middle East and Africa Insider Threat Protection Market Size and Forecast, by Vertical (2024-2032)
9.3.1. Financial Services
9.3.2. Healthcare
9.3.3. Government
9.3.4. Other Verticals
9.4. Middle East and Africa Insider Threat Protection Market Size and Forecast, by Enterprise Size (2024-2032)
9.4.1. Small and medium sized enterprises
9.4.2. Large Enterprises
9.5. Middle East and Africa Insider Threat Protection Market Size and Forecast, by Country (2024-2032)
9.5.1. South Africa
9.5.2. GCC
9.5.3. Egypt
9.5.4. Nigeria
9.5.5. Rest of ME&A
10. South America Insider Threat Protection Market Size and Forecast (by Value USD and Volume Units)
10.1. South America Insider Threat Protection Market Size and Forecast, by Solution (2024-2032)
10.1.1. User and entity behaviour analytics
10.1.2. Data loss prevention
10.1.3. Endpoint detection and response
10.1.4. Security information and event management
10.2. South America Insider Threat Protection Market Size and Forecast, by Deployment (2024-2032)
10.2.1. On-premises
10.2.2. Cloud-based
10.3. South America Insider Threat Protection Market Size and Forecast, by Vertical (2024-2032)
10.3.1. Financial Services
10.3.2. Healthcare
10.3.3. Government
10.3.4. Other Verticals
10.4. South America Insider Threat Protection Market Size and Forecast, by Enterprise Size (2024-2032)
10.4.1. Small and medium sized enterprises
10.4.2. Large Enterprises
10.5. South America Insider Threat Protection Market Size and Forecast, by Country (2024-2032)
10.5.1. Brazil
10.5.2. Argentina
10.5.3. Rest of South America
11. Company Profile: Key players
11.1. Mimecast
11.1.1. Company Overview
11.1.2. Financial Overview
11.1.3. Business Portfolio
11.1.4. SWOT Analysis
11.1.5. Business Strategy
11.1.6. Recent Developments
11.2. IBM
11.3. Netwrix
11.4. CyberArk Software
11.5. FireEye
11.6. Dell Technologies
11.7. Code 42
11.8. Digit Guardian
11.9. Forcepoint
11.10. Sophos
11.11. Fortinet
11.12. Cisco System, Inc.
11.13. Microsoft Corporation
11.14. Broadcum, Inc.
11.15. VMware
11.16. Micro Focus
11.17. Zoho Corporation
11.18. McAfee, LLC.
11.19. Blackberry
11.20. Zoho Corporation Pvt. Ltd.
11.21. Citrix Systems
12. Key Findings
13. Industry Recommendation
















